The software-defined data center is made possible by virtualizing the key components and functionalities of the datacenter. VMware’s NSX-V platform has made tremendous waves in the software-defined data center and has allowed organizations to be truly freed from the underlying hardware network components for data center communication.
VMware’s NSX product has certainly matured over the last several releases with the latest release by the VMware being, NSX-T 2.2
VMware NSX-V vs NSX-T Comparison
NSX-V (NSX for “vSphere”) is designed for vSphere deployments only and is architected so that a single NSX-V manager platform is tied to a single VMware vCenter Server instance. The NSX-V platform is the original NSX platform that has been around for a few years now.
It is specifically designed with VMware virtual machines in mind as that is the legacy virtualization mechanism for workloads that has been around since the onset of server virtualization.
With NSX-V, organizations are able to mobilize network connectivity between virtual machines and allow those workloads to be connected in ways that were otherwise unable to be delivered efficiently by physical networking hardware.
For the most part, if you are wanting to run a software-defined networking infrastructure within the realm of VMware vSphere, NSX-V is the platform that you are most likely to be using.
NSX-T (NSX “Transformers”) is designed to address many of the use cases that NSX-V was not designed for, such as the multi-hypervisors. NSX-T is a multi-hypervisor aware SDN stack brought to the likes of vSphere, KVM, OpenStack, Kubernetes, and Docker.
It is designed to address emerging application frameworks and architectures that have heterogeneous endpoints and technology stacks. One of the major use cases for NSX-T is with containers. In today’s virtualization, we are seeing more and more applications are running in environments outside of virtual machines.
Important as well when considering the multi-hypervisor support is the fact that NSX-T has been decoupled from VMware vCenter Server. NSX-T is a standalone solution for vCenter and vSphere environments but it can also support KVM, public cloud, containers, and can also be integrated into frameworks like Red Hat OpenShift, Pivotal, and others.
One of the major shifts in focus you will see when comparing the two products is that NSX-T is more cloud focused with forward looking functionality.
It also allows organizations more flexibility in choosing the solution that best fits their use case whether that is including hypervisors, containers, bare metal, and public clouds.
It also allows organizations more flexibility in choosing the solution that best fits their use case whether that is including hypervisors, containers, bare metal, and public clouds.
VMware NSX-T is integrated with the VMware Photon Platform which is the cloud centric operating system that VMware developed from the ground up with the likes of the current vCenter server running atop this platform. NSX-T also contains the NSX-T Container Networking interface (CNI) plugin that will allow developers to configure network connectivity for container applications that help deliver Infrastructure as a Service.
Architecture
- Decoupled from vCenter
- NSX-T Manager and NSX-T controllers can be deployed as VMs on either ESXi or KVM
- There is a new “hostswitch” that is utilized for multi-hypervisor support. This is a variant of VMware vSwitch and Open Virtual Switch for KVM
- Utilizes Geneve encapsulation – MTU of 1600 is still recommended for the encapsulation header
- Routing changes – NSX-T utilizes next-generation optimized routing that is multi-tiered with logical separation between the provider router (Tier0 router) and the tenant router function (Tier1 router)
- Standard HTML5 interface for configuration and management
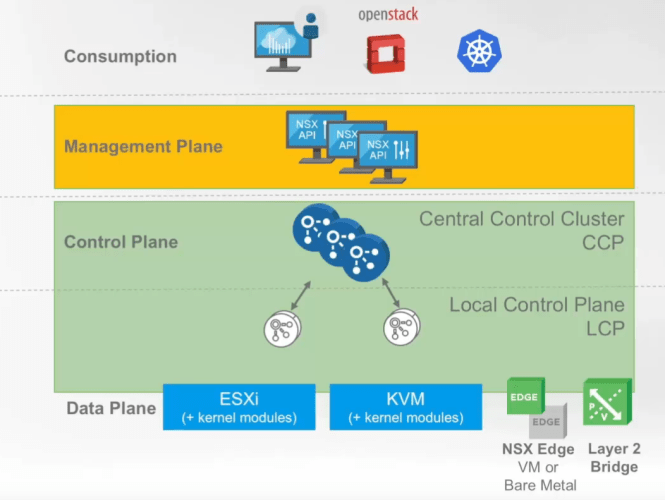
Like NSX-V, NSX-T too contains a management plane, data plane and a control plane
Key Points:
Data Plane
- NSX-T uses in-kernel modules for ESXi and KVM hypervisors for constructing data plane.
- Since NSX-T is decoupled from vSphere, it don’t rely on vSphere vSwitch for network connectivity. NSX-T data plane introduces a host switch called N-VDS (NSX Managed Virtual Distributed Switch).
- All create, read, update and delete operations are performed via the NSX-T Manager.
- Data plane offers features such as Logical routing, Logical switching, DFW, NAT, DHCP etc.
Control Plane
- NSX-T control plane is formed by Central Control Cluster (CCP) + Local Control Plane (LCP) that runs on the hypervisors (Esxi/KVM)
- CCP controller nodes are deployed as VM’s that can run on an Esxi host or KVM.
- Like NSX-V, controllers in NSX-T is responsible for slicing logical switching and logical routing.
Management Plane
- NSX Manager which is deployed via OVA file forms the management plane for NSX-T.
- The management plane handles authentication, monitoring and inventory collection from the compute managers.
- NSX-T manager can be integrated with various Cloud Management Platforms (CMP) via Rest API’s.
- Although vCenter is decoupled from NSX-T management plane, you can add vCenter server as compute manager to leverage vSphere features.
Key Points:
- Designed to work with multiple hypervisors (ESXi and KVM currently)
- Does not rely on vCenter
- Tiered routing
- HTML5 interface is standard
- Openstack plugin allows developers to build and interact with Infrastructure as Code
- Geneve encapsulation protocol

Comments
Post a Comment